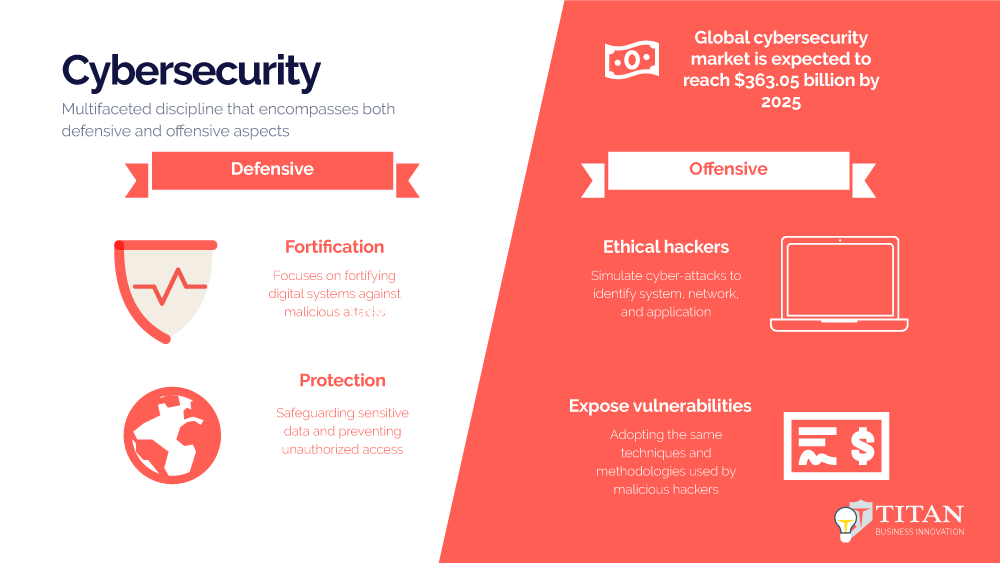
In today's interconnected world, where digital systems play a pivotal role in our personal and professional lives, the importance of cybersecurity cannot be overstated. It is a multifaceted discipline that encompasses both defensive and offensive aspects.
In today’s interconnected world, where digital systems play a pivotal role in our personal and professional lives, the importance of cybersecurity cannot be overstated. It is a multifaceted discipline that encompasses both defensive and offensive aspects. Cybersecurity professionals, including ethical hackers, work tirelessly to safeguard systems, networks, and data from malicious threats while exploring vulnerabilities to strengthen defenses. This article delves into the dual nature of cybersecurity, highlighting the roles of defensive and offensive measures. We will also explore the difference between a cybersecurity engineer and a cybersecurity consultant, along with the certifications that validate expertise in these domains.
Defensive Cybersecurity
Protecting Digital Fortresses Defensive cybersecurity focuses on fortifying digital systems against malicious attacks, preventing unauthorized access, and safeguarding sensitive data. Cybersecurity engineers play a crucial role in ensuring that systems and networks are well-protected. In addition, they design and implement security measures such as firewalls, intrusion detection systems, and access controls to defend against threats. Their primary objective is creating a secure infrastructure to withstand cyber-attacks, mitigating potential risks and vulnerabilities.
Alarming statistics highlight the significance of defensive cybersecurity measures. According to a recent report by Cybersecurity Ventures, cybercrime is estimated to cost the world $10.5 trillion annually by 2025. Additionally, a company’s average cost of a data breach is $3.86 million. These staggering figures emphasize the criticality of defensive cybersecurity and the need for skilled professionals who can effectively protect organizations from cyber threats.
Offensive Cybersecurity
The Ethical Hacker’s Arsenal While defensive measures are essential, it is equally important to adopt an offensive mindset to identify and address vulnerabilities proactively. This is where ethical hackers, also known as penetration testers or white hat hackers, come into play. Ethical hackers are cybersecurity professionals who simulate cyber-attacks to identify system, network, and application weaknesses. Ethical hackers expose vulnerabilities before cybercriminals can exploit them by adopting the same techniques and methodologies used by malicious hackers.
The demand for ethical hackers has skyrocketed in recent years. The global cybersecurity market is expected to reach $363.05 billion by 2025, with penetration testing being one of the fastest-growing segments. A study by the International Data Corporation (IDC) reveals that organizations that hire ethical hackers and conduct regular penetration tests experience 64% fewer security breaches. These statistics demonstrate the critical role played by ethical hackers in fortifying digital defenses and protecting organizations from cyber threats.
Difference between Cybersecurity Engineer and Cybersecurity Consultant
While cybersecurity engineers and consultants work in the cybersecurity domain, there are key distinctions in their roles and responsibilities.
A cybersecurity engineer focuses on the technical implementation and management of security measures. They design, develop, and deploy security solutions, conduct risk assessments, and ensure the proper functioning of security systems. Cybersecurity engineers possess in-depth knowledge of networking, system architecture, and security frameworks. Their expertise lies in building and maintaining secure infrastructures.
On the other hand, a cybersecurity consultant offers strategic guidance and expertise to organizations. They assess an organization’s security posture, identify vulnerabilities, and develop tailored security strategies. Cybersecurity consultants possess a broader understanding of the business environment, regulatory compliance, and industry best practices. They provide recommendations, develop policies and procedures, and help organizations align security practices with business goals.

Certificates and their significance
Certifications in the cybersecurity field validate professionals’ knowledge and skills, enabling them to stay current with evolving threats and technologies. Here are some notable certifications and their meanings:
- Certified Ethical Hacker (CEH): Offered by the International Council of Electronic Commerce Consultants (EC-Council), the CEH certification validates the skills and knowledge required to identify vulnerabilities and perform ethical hacking activities. CEH-certified professionals deeply understand hacking techniques, penetration testing methodologies, and countermeasures. This certification demonstrates proficiency in offensive cybersecurity and showcases the ability to think like a hacker to protect digital assets better.
- Certified Information Systems Security Professional (CISSP): The CISSP certification, provided by the International Information System Security Certification Consortium (ISC)², is a globally recognized credential for cybersecurity professionals. It validates expertise in various domains, including security and risk management, asset security, and security architecture. CISSP-certified individuals possess a broad understanding of cybersecurity principles and best practices, making them valuable assets in defensive cybersecurity roles.
- Certified Information Security Manager (CISM): The CISM certification, offered by ISACA, is designed for professionals responsible for managing and overseeing information security programs. CISM-certified individuals demonstrate competency in information security governance, risk management, and incident response. This certification emphasizes the skills needed to establish and maintain effective cybersecurity frameworks and align them with business objectives.
- Offensive Security Certified Professional (OSCP): The OSCP certification provided by Offensive Security is highly regarded in offensive cybersecurity. It focuses on hands-on practical skills and requires individuals to pass a rigorous 24-hour practical exam. OSCP-certified professionals possess practical knowledge in penetration testing methodologies, network exploitation, and vulnerability assessment. This certification validates the ability to perform real-world cybersecurity tasks and effectively identify and exploit vulnerabilities.
- Certified Information Privacy Professional (CIPP): Offered by the International Association of Privacy Professionals (IAPP), the CIPP certification focuses on privacy laws, regulations, and practices. It validates professionals’ understanding of privacy frameworks, data protection, and privacy program management. CIPP-certified individuals play a vital role in ensuring compliance with privacy regulations, safeguarding sensitive data, and addressing privacy concerns in cybersecurity initiatives.
In the ever-evolving landscape of cybersecurity, the defensive and offensive aspects play complementary roles in safeguarding digital assets. While cybersecurity engineers focus on fortifying systems and networks, ethical hackers identify vulnerabilities before malicious actors can exploit them.
The abovementioned certifications serve as valuable credentials, validating professionals’ knowledge and expertise in various cybersecurity domains. By pursuing these certifications, individuals can demonstrate their proficiency, enhance their career prospects, and contribute to building a more secure digital world. Whether defending against threats or proactively identifying vulnerabilities, the collaboration between cybersecurity professionals and the power of certifications ensures a robust cybersecurity ecosystem.

